Fraud, Smartcards, & Biometrics
© Mercury Communications Ltd - May 1993
![]() 2007
network writings:
2007
network writings:
![]() My
TechnologyInside blog
My
TechnologyInside blog
Magnetic-stripe based credit, debit, pre-paid and calling cards are now in everyone's pocket and it would be very difficult indeed to imagine day-to-day life without them. However, their very technological simplicity is a double-edged sword, bringing convenience to consumer financial transactions on one hand, while on the other, they are directly responsible for creating an annual level of fraud that has reached £160M in the UK alone. In the telecommunications sector, the use of pre-paid cards has been extensive in public call boxes to reduce fraud by removing the use of cash. Also, new mobile services in the form of Global System for Mobile Communications (GSM) and Mercury One2One's Personal Communications Network (PCN), are calling for more 'intelligence' and security embedded in the network.
Services such as these are leading to an ever wider use of smartcards whose functionality is based on an embedded silicon chip rather than the use of a magnetic stripe on the back of the card. Smartcards in their simple form contain only a memory chip but more complex variants can contain microprocessors that are able to execute complex algorithms such as transaction management, data encryption, and authentication. This issue of Technology Watch looks at smartcards and shows how they will provide the linchpin to many of the new telecommunication services to be rolled out in the next decade.
Card Fraud in the UK
The major disadvantage of the simple magnetic strip card lies in the very simplicity of the concept which has lead to financial fraud on a massive scale. According to figures released by the Association for Payment Clearing Services (APACS),card fraud losses grew 35% to £165.6M in 1991 in the UK and according to Scotland Yard it could have been as much as £400M. 75 percent of this fraud took place at the point of sale. Out of the 83 million cards held by 30 million people, two million were lost or stolen in 1991, of which 200,000 were later used for fraud. This means that each stolen credit card scooped an average of £794 for the fraudster. Most are passed to middlemen who know how to get the best use from them. Cheque books with guarantee cards change hands for about £3 per cheque, while credit and debit cards change hands for up to £150. The average loss for a stolen debit card is £647 and for a cheque guarantee card, £387. Although it should be possible to
reduce fraud using smartcards, a big consideration for the banks is at what cost. A recent Mori survey carried out on the behalf of Reader's Digest indicated that customers are only prepared to pay around £2.40 a year extra for safer cards.
One measure of fraud protection introduced by banks for automatic teller machines (ATMs) and Telecommunications Operators (TOs) for calling cards is the personal identity number (PIN). The security of PINs relies on the user keeping their PIN code separate from their card. A recent poll of customers who had lost their cards showed that many had written down their PIN code, something firmly discouraged by banks. Indeed, six percent admitted to keeping their PIN with their card! Among those under the age of 24, the group most likely to have their cards stolen, the figure was as high as 10 percent. In practice, not writing PIN numbers down is easy advice to give but not so easy to adhere to when a user has to remember upwards of five PIN codes!
When PINs are used with calling cards, it is relatively easy for a determined criminal to obtain PIN numbers by illicit means. For example, in a recent 'sting', advertisements were placed in a local London newspaper for an auction of cheap electrical equipment. When the customer arrived they were asked to type in their PIN 'just to check the card is valid'. Within days hundreds of bogus cards were being used to buy goods, withdraw money from cash machines and make international telephone calls. PIN codes given over a telephone line either verbally or via DTMF tones can be recorded easily, especially if a cordless telephone is used.
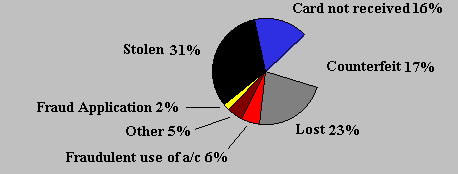
Figure 2 -Visa Fraud Sources to the End of 1992
Because of these problems, it is considered by many that the PIN concept has run out of steam. However, banks in the medium term are likely to commit to introduce the use of PIN codes at the point of sale as the only practicable means of reducing fraud no matter how inconvenient this might be. As we shall later, the use of simple memory cards do act as a deterrent to opportunistic fraud. The fraudulent refilling of pre-paid cards can be minimised by the use of smartcards and there are methods that could be used for personal identity authentication other than PIN codes. These approaches fall under the generic heading of biometrics. Below are some recent fraud issues:
- The French market could provide some guidance for British industry. According to Visa, French card losses, are running at a level of 0.08% of volume, are a third of British levels.
- Bell Canada has suspended all overseas calling card activity from coin accepting pay phones.
- Visa International has write-offs in the Middle East and Africa region that have risen from $26M in 984 to $242M in 1992.
- Midland bank have considerably cut Switch card interception by delivering cards by Securicor.
- South Africa accounted for 71% of the estimated credit card losses by Mastercard in 1991.
- AT&T have had success in reducing calling card fraud by watching for abrupt changes in cardholder behaviour. This uses computer models to search for suspicious patterns off-line .
- In Norway 500,000 smartcards have been issued and banks in France are planning to convert all their bank cards to smartcards by 1995.
- In March 1993 several UK banks are running experiments to reduce fraud by placing laser-etched photographs on credit cards. At least one is claiming significant success with the approach.
Simple Magnetic Strip Cards
The simple 85 x 54 x 0.8mm magnetic stripe credit or calling card has been in wide use for many years. Its physical size, required robustness, and electrical characteristics are all defined in a series of International Standards Organisation (ISO) standards that begin with ISO 7810; "The design, construction and use of identification cards". Data is stored in a 12.5mm wide strip of a ferrous compound which is similar to the material used for audio recording in cassette tapes. The strip usually contains three data tracks, although a narrower strip, with only two tracks, is sometimes encountered. Tracks one and three contain 8.27bits/mm or a total of 634 bits. Track 2 contains 2.95bits/mm or 226 bits. Track 3 appears to be a read/write track, while tracks 1 and 2 are read only. A supplementary specification aimed at financial transactions states that track 1 contains a total of 79 characters that includes a 3-character country code, a 2-to-26 character name, a 4-character expiration date, and a 3-character service code. Track 2 contains 40 characters that includes a 19-character identificationcode, a 3-character country code, a 4-character expiration date, and a 3-character service code. It looks like track 1 was defined by the financial industry while track 2 was defined by the airlines - i.e. in-built duplication!
As the card is manually swiped through a reader, data is formatted so that it can be recovered no matter whether the card is swiped from left to right or vice versa. Moreover, the card can be read no matter at what speed the card is passed through the reader. The encoding technique is very simple and all that is needed to read an average card is to purchase a simple read-head assembly which only costs £20.00. This can be connected to the serial port of any personal computer. A read/write assembly is a little more expensive at £400.00 but is still easily obtainable. A standard ISO card costs in the range of £0.08-£0.30, depending whether printing involves the addition of embossed text, engraving, thermal printing, holographic watermarks, or other techniques used to reduce fraud.
The advantages and principal disadvantage of magnetic cards are easily stated:
- Accepted throughout the world
- Cheap to manufacture
- Wide-scale fraudulent use (disadvantage)
Smartcards
Are smartcards some new whizzy new piece of technology looking for an application? No! Smartcards are now at the heart of many new services and provide a vital function.
What is a smartcard?
A smartcard is simply a plastic card of similar size to a credit card that contains a silicon chip, access to which is made through gold plated contacts. It is thus called a contact card. An example of this type is shown in Figure 1. In this case the chip contains 256 bytes of Electrically Erasable Programmable Read Only Memory (EEPROM) and would have similar functionality to a magnetic stripe card. Another type of card is a contactless card which is constructed in much the same way as a contact card but contains two small coils of printed copper. When in the presence of a strong RF or magnetic field these coils generate a voltage that is used to power the chip. The RF is also used as a bi-directional data path at data rates in the range of 300 to 9,600bit/s. Figure 3 shows the cross section of a typical contact smartcard. The integrated circuit (IC) is inserted into a cut-out in the PVC core and bonding wires are passed through the card to connect the IC pads to the card connectors. The IC assembly is sealed with epoxy resin and the whole card is polymerised to provide rigidity and to protect it from the atmosphere.
The level of 'smartness' in the card depends on what IC is embedded in the card. Simple memory cards contain only EEPROM memory which means that data can be stored and changed, ideal for a pre-paid calling card service. Data is remembered when the card is removed from the power source as provided in the read/write terminal.
Smarter smartcards not only contain memory but a microprocessor as well. It is now possible to embed in a smartcard as much processing power as was seen in a small personal computer several years ago. All this power can be used to undertake computationally intensive algorithms such as DES encryption, discussed in TW #11, RLE compression algorithms, as discussed in TW #8, or biometric person identification, as discussed later.
What is the cost of all this 'smartness'? A magnetic card costs between £0.08 and £0.30 in high volume, a memory only smartcard costs around £0.50, while a complex microprocessor based card can cost upwards of £3.50. 'Super' smartcards that contain memory, a microprocessor, LCD display and a keyboard cost around £20.00.
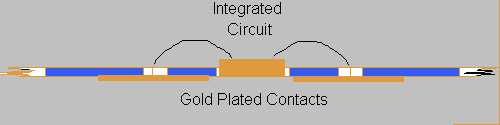
Figure 3 - The Construction of a Typical Smartcard
Advantages of a microprocessor based smartcard over a memory smartcard
It is clear that the use of a memory smartcard brings distinct advantages in fraud prevention such as making the refilling of discharged pre-payment calling cards virtually impossible. The addition of a processing capability brings many other benefits over and above this in that they are able to respond 'intelligently' to user question and answer sessions, for example:
- Smartcard software can be updated at any time during an on-line session. For example, in the BBC's Select service, which transmits encrypted video and sound training programs on BBC-1/2 in the middle of the night, smartcards manage the encryption. If at any time the encryption algorithm is compromised, a new encryption seed code can be sent down to all the decoders at one time. In fact, this facility is so flexible that the BBC can stop elicit veiwing with a stolen card by turning off only the stolen card's decryption software.
- Smartcards can implement anti-fraud techniques through biometric techniques such as storing fingerprints.
- Smartcards are on-line configurable. A user can have their cards upgraded at any time to allow them access to new services for which they have subscribed. What is more, they can obtain instant access to new services.
- Users can define their own PIN numbers, its length, exact format, and can redefine it any time they wish. This is an excellent way of stopping users from writing down their PIN codes on scraps of paper as they can use an alpha/numerical sequence that has some significance to them alone.
- To improve security, following a successful entry of a PIN code, subsidiary questions can be asked such as date of birth or details of the last transaction.
- Smart cards are being designed with fusible links. Once a card has been programmed or a pre-payment card debited to its limit, fuses are blown to prevent unauthorised access or refilling.
- Local processing on smart cards reduces the amount of processing that needs to be done by the PSTN or mobile network's Intelligent Network (IN) software. Instead of using network based IN to achieve a simple number translation, this can be handled locally by the smartcard.
- Smartcards can contain a personal telephone number so when a card is transferred from one terminal to another the network follows it and automatically transfers the call to the new terminal. This utility is at the heart of the new digital mobile service GSM and PCN. The concept is not only applicable to mobile services but for fixed networks as well if a smartcard facility is built into the telephone or pay phone.
- When used for computer access control, smartcards can store which applications a user is authorised to access and can also store the user's preferred operating environment or desktop configuration.
Two Real TelecommunicationSmartcard Applications
It is predicted that some 160 million smartcards will be issued in the next three years, here are two applications that will realise that prediction.
Global System for Mobile communications (GSM)
GSM is the new digital replacement for the current analogue generation (TACS, NMT etc.) of mobile communication. The benefits of digital technology are principally improved quality of service in the areas of voice quality and connection robustness. But other principal benefits are improved security and personal mobility. Authentication is essential to guarantee that the subscriber is genuine and that the card is not a fraudulent copy, nor that it has been reported stolen. In recent years the analogue mobile networks have been subject to high fraud levels whereby the user's identification code burnt into a chip in the mobile handset is recorded off-air at the initiation of a call using of a scanning radio. This code is then burnt into a chip and placed into another mobile telephone. From that point on, all the calls made on that mobile are charged to the real, and until he gets the bill, ignorant subscriber. This can only be rectified 'back at base' by changing the chip in the original handset and blocking the calls from the rogue handset.
So what does a GSM smartcard, known as the subscriber identity module (SIM), do? Its primary task is to undertake encryption of voice and data and to manage authentication. The subscriber can enter his own PIN number onto the card and use this when making a call. There is also a Personal Unblocking Key (PUK) that allows the subscriber to redefine the PIN when it is blocked following three incorrect entries.
From the user service perspective, the most important aspect of the SIM is that when it can be plugged into any GSM phone, that phone immediately becomes yours. It checks that the subscription is valid and that the SIM has not been stolen, by authenticating the call right back to the users home location register , (HLR), database located in the management service centre, (MSC) . This concept means that the subscriber can use any GSM phone anywhere in Europe to make or receive calls and still be billed to his/her home. Thus it is now possible for a car manufacturer to pre-install a GSM telephone into a car during manufacture as it will only be activated by the insertion of a subscriber's SIM smartcard. With GSM, the SIM is inserted into the handset and must stay inserted for the complete time the subscriber is using that particular handset.
There are other advanced features in the GSM network underpinned by the SIM:
- The SIM card can hold up to fifty abbreviated dialling codes.
- Selection of used language. Although only due for definition in the next round of GSM standards, a user will be able to select the system language, an important facility for the European wonderer.
- Advice of charge meter. Based on tariffs held in the SIM, downloaded from the network, the subscriber can display the real cost of the call in real time.
- The GSM system supports short message transmission. If a subscriber's handset is inactive when a message is received, it is stored in the HLR until his/her phone is activated again. When this occurs, the message is downloaded to the subscriber's current location where it is stored in the SIM card. Up to five, 160 character long, messages can be stored at any one time. The subscriber can access these messages at any time.
Personal Communication Network (PCN)
Mercury One2One's PCN network is based on a subset of the GSM technical specifications called DCS 1800. A PCN network is aimed at placing calls with a person rather than a location. This is achieved by implementing microcells that enable the use of lower transmit powers, hence smaller and hopefully cheaper, handsets.
The functionality of the SIM card in a PCN application is virtually the same as that described for GSM. It again provides security and mobility through the use of a smartcard plugged into the side of the handset.
PSTN Intelligent Networks
It can be observed from the list of services listed for GSM and PCN, that the smartcard performs a vital function in the mobile network. It is closely linked to, and integrated with, Intelligent Network (IN) services that support personal mobility, security, and advanced ease-of-use features.
The GSM inventory of features would also be seen as advantageous on a fixed PSTN network. Most of these features could be implemented using a classical CS-1 network-based IN architecture, but this approach might be considerably enhanced through the use of a smartcard connected to the telephone. Further, most visions of future telecommunications, involve the ability to use a common personal number on either a fixed PSTN network, or a mobile network. Is not now the time to seriously consider the use of smartcard technology on fixed networks? And, would it not make sense to consider smartcard compatibility with new PCN networks to support true personal number mobility? The addition of a smartcard to the domestic phone and/or pay phone could be deemed as both sensible and smart!
There are many other examples of the use of smartcards in the UK. In November 1992, Whitbread began a trial of prepaid smartcards in twelve public houses. The new Sega World leisure centre in Bournemouth looks set to use smartcards. In Scotland, a new golf driving range opened in 1992 which uses prepaid smartcards where one golf ball equates to one unit of stored value. Most UK banks including Barclays, TSB, National Westminster and Lloyds, have now implemented remote banking systems for their business customers which use smartcards to ensure that only authorised personnel can view banking records and initiate financial transactions. There are also several examples of their use in public transport, public utility, vending machine, and pay TV markets.
Biometrics
All the applications of smartcards detailed above suffer from one significant problem: actually verifying that the presenter of a card is actually person who owns it. As we have seen, PIN codes are not infallible. This is where biometric technology comes to the fore. Biometrics is the umbrella term that encompasses personal verification based on electronic identification of the card presenter using body features. These include fingerprints, hand geometry, retina prints, and signature analysis.
Over the past few years biometrics has leapt into the vocabulary of most bankers, especially when discussing fraud. Late last year Barclays Bank issued a Biometric Requirement Document to potential equipment suppliers tying down for the first time the parameters by which any biometric verification unit would be judged. It included the following minimum conditions:
- False reject rate: 1 in 100,000
- False accept rate: 1 in 20
- Speed of verification: < 3 seconds
- Cost of unit: < £150
These criteria are seen to be very tough to meet and there are currently no individual biometric systems that can meet all criteria, although there are some that meet several of the requirements. The current leader of the biometric pack is fingerprint recognition.
Fingerprint Recognition
Fingerprints are at the top of the list as far as workable systems are concerned, although, at least in the UK, the technique is irrevocably associated with criminals. It is a fair bet though, that within a few years we will all become used to fingerprint verification systems used in access control or point of sale locations.
Fingerprint verification systems are based on an analysis of the unique features of an individual's fingerprint. Figure 4 shows the main classes of fingerprint: 5% of the population have 'Arch' type prints, 30% have, 'whorl', 64% have 'simple loops', and 1% have 'composite' prints.
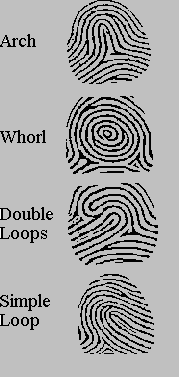
Figure 4 - Fingerprint Classes
Fingerprint verification systems, such as those demonstrated by Bull's Telesyncro subsidiary and a small UK company called Printscan, use a solid-state scanner to input a fingerprint into the microprocessor for analysis. The fingerprint algorithm typically splits the scanned image into a number of sectors (the standard FBI algorithm calls for sixteen), and a count of certain features and their position relative to each other, in each sector is listed. This information is then compressed and stored on the smartcard. Interestingly, the Printscan system can compress data down to a few hundred bytes so that it can be stored on an ordinary magnetic card. The Bull Telesyncro system compresses down to around 2,000 bytes and stored on a standard 2,048 memory card. Incidentally, it is not possible to reconstitute the print from the data stored on the card.
The use of both systems is straightforward and quite reliable although they do not, as yet, quite meet the tough demands of the banks. The Telesyncro system has recently proved its credentials by being successfully used as the access method at EXPO in Spain. It should be remembered that there are problems with certain sections of the population. Pipe smokers, for example damage their fingertips when they pack down their tobacco; miners and bricklayers can wear down their skin; and young children and old age pensioners present problems with smooth skin, and women that use hand cream also present problems. Even with these limitations, it might not be too long before we are all used to 'presenting our finger' prior to making a card transaction.
Signature Analysis
Signature analysis systems generally measure writing pressure, acceleration, direction and speed. Essentially the problem is that each time a signature is written it is written differently. This means that when all the measurements are taken of a presented signature, a calculation is needed to see how close it is to the pre-stored template. An error of + or - 2% is generally acceptable. Many leading companies have lodged patents in this area including IBM, NCR, and even VISA. But in 1993, signature analysis is insufficiently reliable and still requires an excessive amount of computational power to make the system workable in low-cost card applications.
The use of biometrics seems to be in a sort of limbo. According to biometric systems equipment designers, banks are presenting what they see to be an unachievable specification. At the same time the banks seem to be unwilling to commit to a solution that would solve the £160 million fraud problem. Maybe it is because they are unsure of their customers reactions, especially if they did not all move in unison.
The Issues
There are several interesting issues that TOs need to wrestle with in respect to the use of smartcards.
- With the overall level of fraud steadily rising, has the time now come to bite the bullet and consider smartcards for use as telephone pre-paid cards rather than magnetic cards?
- The mobile communications industry recognised the advantages to be gained by using a sophisticated smartcard many years ago, although systems are only just starting to be deployed. Is it not wise to recognise that PSTN networks will need similar functionality in the future and that smartcard functionality at the customer premises equipment (CPE) level will need to be considered in parallel with the deployment of network based IN?
- Recognising that the new digital mobile services are the first real implementors of IN networks to support true personal number mobility, would it not be wise for partnerships to occur between mobile or PCN operators and PSTN operators to synergistically offer identical roaming services whether using a portable PCN handset, a PSTN network telephone, or public pay phone?
Smartcards are typical of many technologies that have had a long history but few takers. Their day has at long last come.
